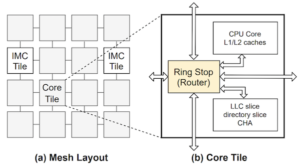
MIT Researchers Warn of Interconnect Security Vulnerabilities, Propose Mitigation Strategies

Researchers at MIT have developed new software mitigation techniques for a hardware-level security vulnerability uncovered in on-chip mesh interconnects.
On-chip interconnects enable communication between the processor cores, and the vulnerability lies in situations when programs run concurrently on multiple cores. Delays can occur when multiple cores use the same interconnect to transmit data across the chip, and malicious agents can use these delays for what are called “side-channel attacks” where encrypted information can be stolen from elsewhere in the system.
The MIT researchers studied these attacks by reverse-engineering on-chip interconnects and investigating how the flaws work. Through this inquiry, they formed an analytical model of how traffic flows between the processor’s cores which helped them design and deploy their own side-channel attacks. With this inside-out knowledge, the team was able to develop two mitigation strategies that improve security with no physical changes to the chip.
“A lot of current side-channel defenses are ad hoc — we see a little bit of leakage here and we patch it. We hope our approach with this analytical model pushes more systematic and robust defenses that eliminate whole classes of attacks at the same time,” says co-lead author Miles Dai in an MIT News article.
For their research, the MIT team built an analytical model of the processor that summarizes how traffic flows on the interconnect. According to coverage from MIT News, in order to do this, the researchers first “discovered that the interconnect is like a highway, with multiple lanes going in every direction. When two traffic flows collide, the interconnect uses a priority arbitration policy to decide which traffic flow gets to go first. More ‘important’ requests take precedence, like those from programs that are critical to a computer’s operations.”
The resulting analytical model identifies which of the processor’s cores are most vulnerable to side-channel attacks, which are usually the cores that can be accessed through the most lanes of traffic on the chip. By selecting the core most susceptible to an attack, hackers can monitor it to withdraw sensitive information.
“If the attacker understands how the interconnect works, they can set themselves up so the execution of some sensitive code would be observable through interconnect contention. Then they can extract, bit by bit, some secret information, like a cryptographic key,” co-lead author Riccardo Paccagnella told MIT News.
Using their model, the team launched their own side-channel attacks that were able to steal full cryptographic keys from two different programs. Through further investigation of these attacks, they designed their mitigation mechanisms.
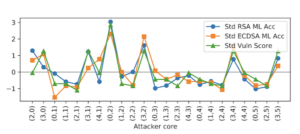
This graph shows the correlation between standardized analytical model vulnerability scores and standardized observed attack accuracies across all attacker core placements. Source: Dai, et al.
The first mitigation technique involves using the analytical model to pinpoint the most vulnerable cores and then scheduling sensitive software to only run on less vulnerable cores. The second mitigation tactic involves an administrator reserving cores around a sensitive program and only running trusted software on those cores.
As a result of their research, the MIT team greatly decreased the accuracy of side-channel attacks using these mitigation strategies. Since no physical changes to the hardware are needed, the researchers are confident these strategies can be easily deployed. The greater security may, however, come with a performance penalty as higher-risk cores are taken out of play, but the impact should be minimized in modern cloud environments, where resources are often overprovisioned, the team concludes.
The authors anticipate more research on interconnect security which they say remains an overlooked attack surface.
This project was carried out by graduate students and co-lead authors Miles Dai of MIT and Riccardo Paccagnella of the University of Illinois at Urbana-Champaign, as well as Miguel Gomez-Garcia of MIT; John McCalpin, a research scientist at Texas Advanced Computing Center; and senior author Mengjia Yan, the Homer A. Burnell Career Development Assistant Professor of Electrical Engineering and Computer Science (EECS) and a member of the Computer Science and Artificial Intelligence Laboratory (CSAIL).
To learn more about this research, find the scientific paper here.