‘Open Season on Open Source,’ Supply Chain Survey Warns

via Shutterstock
Open source software development is thriving despite the pandemic, with a new supply chain survey estimating a record 1.5 trillion downloads this year of open source components and containers.
In its annual report on the state of the software supply chain, security specialist Sonatype foresees no let-up in the shift to open source tools, noting that up to 90 percent of the code components used by developers are widely available. That all-time high is occurring despite what the company describes as a “massive increase” in software supply chain attacks.
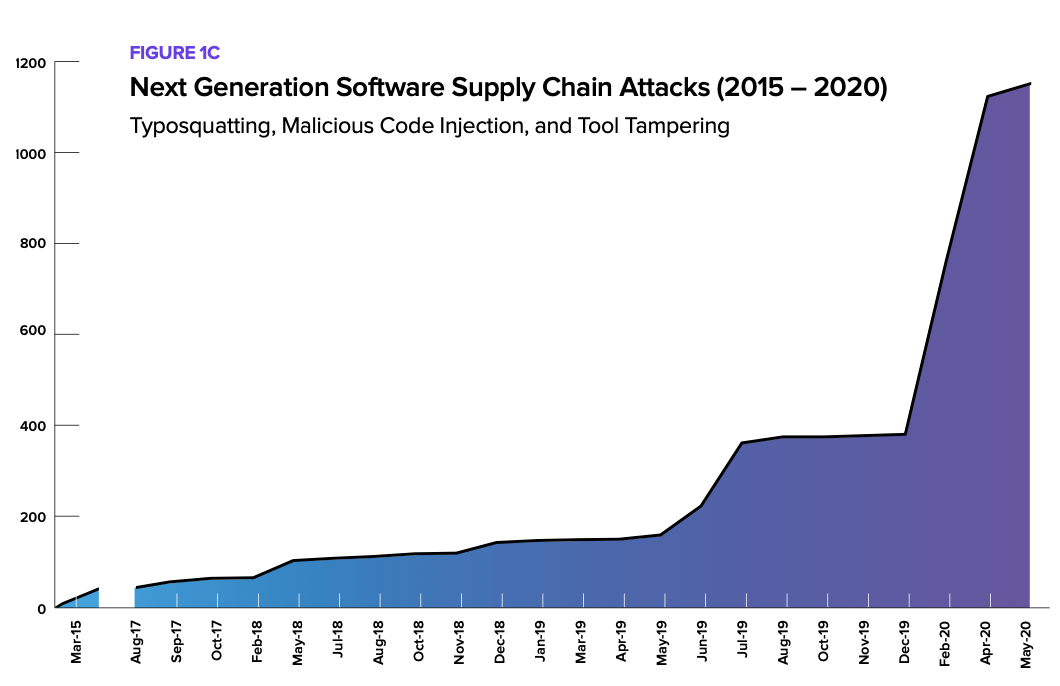
Developers appear undaunted as the sophistication and number of cyberattacks on the supply chain surges, up 430 percent over the last 12 months, the company reported on Wednesday (Aug. 12.) “It’s open season on open source,” the survey concludes. The next generation of attacks are “a uniquely efficient way for adversaries to gain leverage and scale by exploiting software supply chains.”
Those attacks include embedding malware directly into open source projects. “By shifting their focus ‘upstream’, bad actors can infect a single component, which will then be distributed ‘downstream’ using legitimate software workflows and update mechanisms,” Sonatype warned.
The survey notes that European security researchers have discovered that popular code repositories that attract thousands of developers have morphed into a “reliable and scalable malware distribution channel.”
Those researchers note that Node.js and Python repositories have emerged as primary targets for malicious packages, owing in part to the ease of triggering malicious code during package installation.
What’s more, the survey found, open source projects often incorporate at least hundreds of dependencies from other projects, each containing known vulnerabilities. The sheer volume of open source usage combined with exponential growth in dependencies makes it difficult to evaluate the security of each new version of a dependency.
Among the most common and fiendishly simple attacks is “typo-squatting,” which requires nothing more than a developer erroneously typing a component name during a repository search. Those typos can then be used to install a malicious component with a similar name.
Other common attacks include malicious code injection, facilitated by stealing a maintainer’s credentials or launching malware during a new version release to a public repository. “When malicious code is deliberately and secretly injected upstream into open source projects, it is highly likely that no one knows the malware is there, except for the person who planted it,” the Sonatype survey warned.
Downstream attacks can then be launched once the malicious code enters the software supply chain, the authors added.
The survey estimates that one in ten open source software downloads are vulnerable, with more than 10 percent of billions of downloads containing at least one known vulnerability.
Some enterprises security practices are beginning to address open source software vulnerabilities. The survey notes security-minded developers are deploying more frequently, detecting and remediating vulnerable components and approving new open source software components more efficiently.
As open source software continues to make inroads in enterprise infrastructure, developers will have to hustle just to keep up with the next generation of cyberattacks.
Related
George Leopold has written about science and technology for more than 30 years, focusing on electronics and aerospace technology. He previously served as executive editor of Electronic Engineering Times. Leopold is the author of "Calculated Risk: The Supersonic Life and Times of Gus Grissom" (Purdue University Press, 2016).