Updated: Worm Hits Docker Containers

via Shutterstock
A crypto-jacking worm, so-called because it spreads in spurts among unsecured images on servers, is said to be the first detected using Docker application containers.
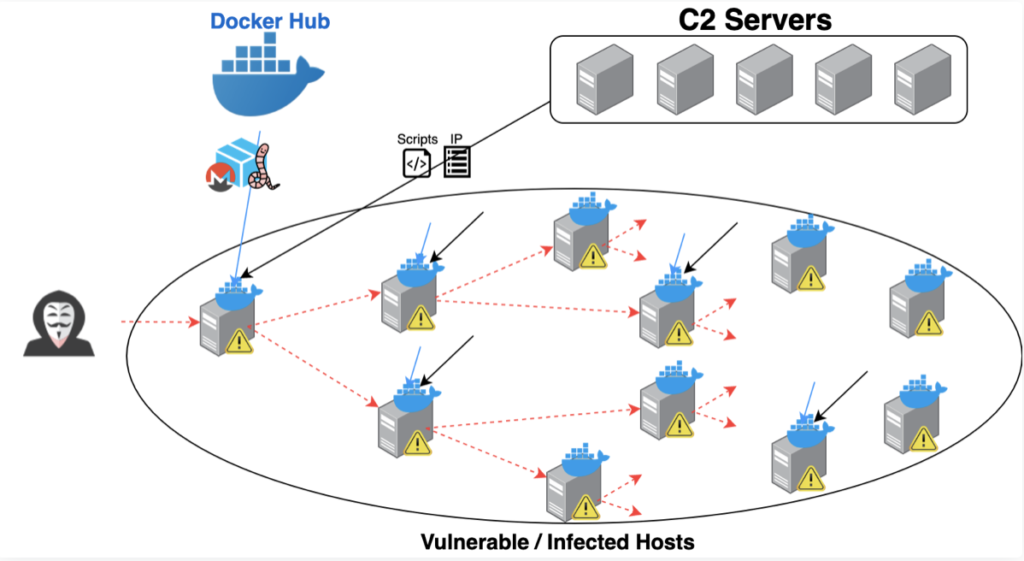
Palo Alto Network’s (NYSE: PANW) threat intelligence team known as Unit 42 reported the exploit dubbed Graboid this week, identifying it as the “first-ever crypto-jacking worm found in images on Docker Hub,” the service for sharing container images. Specifically, the researchers said the worm was found in the community edition of Docker Engine.
They noted that security software generally does not inspect data inside application containers, making malicious activity difficult to detect. The worm is thought to have entered through unsecured Docker daemons, where a Docker image was initially installed. Once downloaded, the malware spreads on the compromised host via servers, spreading from one vulnerable host to the next.
In a statement, Docker said it removed the malicious images from Docker Hub immediately after being notified by Palo Alto Networks. "The default setting for Docker Engine is to deny remote access which prevents this type of attack from occurring, and our documentation strongly discourages leaving a host unsecured," added Justin Cormack, Docker's lead security specialist.
Cormack noted that security steps for connecting with a remote daemon were added to a recent community version of Docker Engine. "It’s also always important to enact best practices when pulling images by making sure the content is trusted and that it runs what it is intended to run," Cormack said. "Docker Enterprise is not affected as it configures secure access to the Docker Engine."
Unit 42 estimated that more than 2,000 unsecured Docker engines were exposed on the web. “Without any authentication or authorization, a malicious actor can take full control of the Docker Engine [Community Edition] and the host,” the researchers said. “The attacker leverages this entry point to deploy and spread the worm.”
“There have been incidents of crypto-jacking malware spreading as a worm, but this is the first time we see a crypto-jacking worm spread using containers in the Docker Engine (Community Edition),” they noted in blog post.
“There really isn't a good reason to expose the Docker engine in this way—it's almost certainly a configuration mistake on the server and the network firewall—if there is a firewall at all,” said Connor Gilbert of StackRox, a container and Kubernetes security specialist. “Leaving the Docker engine API server exposed without authentication lets people run whatever containers they want on your server if they can contact it.”
Given the distributed nature of application containers and the Kubernetes cluster orchestrator, security specialist note that API servers must be secured to fend off malware attacks such as Graboid. Misconfigured Kubernetes clusters also are vulnerable.
“This threat's ability to spread is limited by the number of exposed Docker daemons it discovers, that is Docker daemons that have an internet accessible API without any authentication,” added James Condon, research director at cloud security vendor Lacework.
“Graboid can jump from infrastructure to infrastructure provided there is an appropriate target,” Condon added. “Docker daemons aren't exposed this way by default. However, sometimes they are initially misconfigured for ease of use, initial deployment and testing. Over time they may become overlooked or forgotten.”
Meanwhile, the Unit 42 researchers warn that a more sophisticated worm attack using a similar infiltration technique “could cause much greater damage, so it’s imperative for organizations to safeguard their Docker hosts.”
--Editor's note: This story has been updated to include a statement from Docker.
Related
George Leopold has written about science and technology for more than 30 years, focusing on electronics and aerospace technology. He previously served as executive editor of Electronic Engineering Times. Leopold is the author of "Calculated Risk: The Supersonic Life and Times of Gus Grissom" (Purdue University Press, 2016).