Hacking Team Sets New Attack Vectors

Most people have now heard about the hack and subsequent release of 400 gigabytes of internal data from Italy's Hacking Team, whose mission is to employ a small group of sophisticated hackers and programmers to develop customized malware for the purpose of intelligence gathering against desired targets. The company markets its services to government entities around the world, which then deploy the software against targets of interest.
The Hacking Team's primary product is the Remote Control Software (RCS) program. Its purpose is to collect information on unsuspecting targets: websites visited, keystrokes pressed, screenshots, video and audio collection from the camera and microphone, and other identifying information such as Geo-IP coordinates.
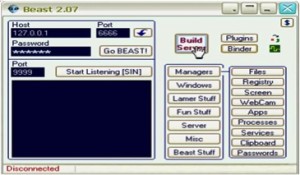
Software with such capabilities are typically known as Remote Access Trojans (RATs), and these types of hacking tools have been around for decades. One of the earliest RATs was the Beast Trojan, which targeted Windows 95 computers and had features closely resembling those of the RCS platform: screen monitoring, keystroke capture, webcam monitoring, and saved passwords.
RATs have long been valuable to attackers for their ability to help uncover juicy information from the users of infected machines. Identities, bank records, employment login credentials, passwords, and personal effects such as photos and videos all become accessible to the attacker once a victim’s computer has been successfully compromised.
The information disclosed within the Hacking Team breach highlighted a number of novel methods the company employs to help facilitate the delivery of the RCS surveillance software to unsuspecting users.
Various publications have reported on the discovery of unpublished exploits, which were uncovered in the trove of documents. The exploits, known as zero-day exploits for their ability to penetrate fully patched systems, targeted Adobe Flash player and would have allowed attackers to install the RCS product without any noticeable change to users’ computers. Software vulnerabilities against widely distributed software are of great interest to attackers, thanks to the strong likelihood of successful exploitation against desired targets.
Other installation methodologies for RCS include the use of a device known as the Injection Proxy Appliance (IPA). The company described it as an ‘offensive security device developed to perform remote installation of the Remote Control System either on LANs or intra-switch segments.’ The system is capable of embedding, on-the-fly, the RCS software or exploits code into webpages, automatic upgrades or any other download.
This hardware appliance is designed to sit within a network environment, and once deployed, it can intercept legitimate Internet traffic and inject malicious code on the return path. This could be done for the purpose of malware delivery, the collection of information, or deceit. The system is also capable of man-in-the-middle attack techniques, which allow for the seamless injection and interception of otherwise encrypted communications — for example, banking credentials.
Man-in-the-middle attacks occur with the intruders first designing webpages that look exactly like the encrypted webpage of a particular interest – for instance, a banking website. When the user visits that webpage, the attacker can seamlessly insert the maliciously crafted webpage in exchange for the real thing. When the user inserts their username and password into the login fields, the information is funneled to the attackers instead of the institution that was originally intended. This well-known attack methodology allows for the collection of difficult-to-acquire information.
But what happens when the attacker can’t gain physical access to the computer, or install a network appliance to the LAN where the computer operates? Well, for that scenario, Hacking Team developed a ‘patent-pending’ module known as Network Injector (NI).
NI is a robust hardware solution that is capable of being installed anywhere upstream from the computer of interest. This includes local LAN environments, all the way up to the ISP level. The designated purpose of NI, according to the Hacking Team, is to ‘install RCS Agents over the Target’s Internet connection by using patent-pending injection techniques and a proprietary streaming melting technology’. The document titled ‘Remote Control System 9 Keynote Presentation’ details the vast capabilities of the system and uses the tagline “Distribute your data across cities. 1 - 10000 targets. It makes no difference.”
After delivery of the RCS product, maintaining a prolonged, undetected presence on the computer would be a primary objective. One ingenious method to achieve this goal is the implementation of a Unified Extensible Firmware Interface (UEFI) rootkit. UEFI is a BIOS replacement responsible for helping to boot the computer to a usable state. Without BIOS or UEFI, the computer has no instructions on which devices to boot, where the operating system resides, or what devices are connected. The code responsible for this task resides in modules located on the motherboard. One simple reason for this is to allow hardware to be easily swapped without requiring extensive reconfiguration of software instructions. This includes hard drives.
By developing a UEFI rootkit, Hacking Team created a methodology to ensure that even in the event of the reinstallation of the OS or the replacement of a hard drive, the RCS product can easily be reinstalled via this difficult-to-detect attack vector.
Hacking Team has developed a robust architecture and employed novel infection vectors for the deployment of the RCS RAT. Considering the complex methodology the company developed to install the software, few would be able to protect against direct attacks.
The breach of the Hacking Team network demonstrates the strong desire for the type of surveillance software being marketed. And while some may concern themselves with the overall security of their computer systems due to the effectiveness of such attacks, others will take solace in the fact that such technologies are helping national security by enabling the surveillance of individuals deemed potentially dangerous.
Adam McNeil is a Malware Intelligence Analyst with Malwarebytes. He has over 10 years of experience analyzing malware and researching online scams and fraudulent behavior. Follow the company on Twitter @Malwarebytes
Related
Managing editor of Enterprise Technology. I've been covering tech and business for many years, for publications such as InformationWeek, Baseline Magazine, and Florida Today. A native Brit and longtime Yankees fan, I live with my husband, daughter, and two cats on the Space Coast in Florida.