Tools Reveal Enterprises’ Dirty Little Cybersecurity Secrets

Many companies have good intentions to fix and address their cybersecurity issues, yet when they see the price tag to implement cybersecurity, firms may buckle under budget pressure. They state they are there to run a business and no longer feel emotionally strong about cybersecurity. We call this kicking the cybersecurity can down the road. This philosophy prevails until an unplanned cyber event or compliance mandate drives the company to fix the existing cybersecurity issues.
Now imagine if a couple of businesses publicized your company’s dirty laundry on the Internet. These firms use so-called sink-hole technology to monitor all public Internet traffic that enters and leaves your business. This is the new era of monitoring and any company’s cybersecurity performance can be observed without going past firewalls, servers, or user systems — and it is perfectly legal.
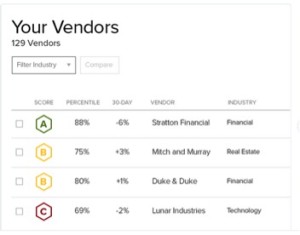
The days of ignoring cybersecurity are long over. Insurance companies, third-party vendors, prospective customers, sales people, and investors evaluate companies' cybersecurity postures. Hiding any cybersecurity problems are over as the spotlight is now on every company. Sink-hole technology uses TCP traps and filters at major Internet connection points with the Internet Service Providers (ISPs) to monitor everybody’s traffic. Nobody can stop this technology or request an exclusion from being monitored since traffic is consider public Internet. If your company has viruses, spamming software, botnets, or malware, the world is going to know because it may be beaconing from your company’s perimeter firewalls across the Internet and to known malicious countries, IP addresses, and servers across the globe. Risk-ranking companies BitSight.com and SecurityScorecard.com monitor malicious activities, trend this data over periods of time, and assign scoring processes ranging from A to F and FICO type scores, with 900 being the highest cybersecurity rating.
Both BitSight.com and SecurityScorecard.com correlate the data of who IP addresses belong to and associate the IP address to the company to build profiles. Over time, Internet traffic is monitored, analyzed, and reviewed to correlate and build vulnerability profiles of each company. This data will show vulnerabilities a company has exposed to the Internet (i.e. company website, assigned IP addresses, portals your customers connect with, and so on). In addition, malware traffic that is beaconing from a company to unknown destinations will clearly indicate malicious activity that may be stealing data from a company. The more malware an enterprise has, the lower its score. Another factor for a lowered score: Prior security breaches, with links to press releases. The face of US corporations will change very quickly because companies that have ignored cybersecurity risk will no longer have a cover to hide cyber problems and issues.
Some investors believe there is a direct correlation between solid company management performance with a strong cybersecurity posture and a lousy executive leadership team with a poor cybersecurity posture. The rationale: investors already know companies will overstate revenue performance to keep shareholders engaged, yet behind the scenes they may not properly invest capital to protect against cyber risk because they want lean business operations. This, in turn, could place the entire investment at risk because of a future cybersecurity breach, threatening the organization (and investment). Most businesses focus purely on revenue and keeping expenses as low as possible; while this may appear a reasonable way to run a business, ignoring cybersecurity risk jeopardizes both revenue and expense management.
When a company explores cybersecurity insurance for a company, the underwriter will visit a ranking website to look at the cybersecurity performance and history to make insurance premium decisions. A company that makes very little effort to maintain good cyber hygiene will have a higher insurance premium compared with one that has made investments to manage cybersecurity risk. Not investing in cybersecurity is no longer an option for companies that want to mitigate cybersecurity risk to the insurance underwriter. Insurance companies are not going to accept high-risk customers without very high premiums.
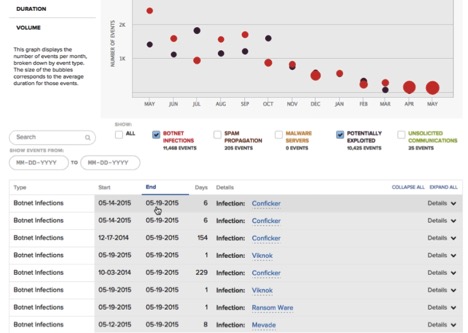
What a past poor performing company looks like from a cybersecurity perspective below with gradual improvements:
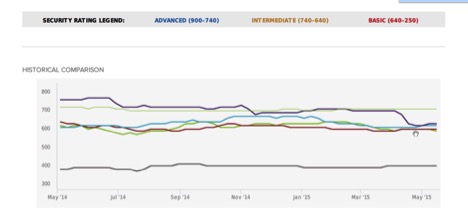
How companies are going to be tracked in the future. Each line color represents a different company on their security posture (companies names have been removed). This allows other companies to monitor the cyber performance of service providers, vendors, and business partners:
What does the pricing look like if you wanted to monitor a business partner or assess third-party risk? The typical starting price to monitor one company starts in the $2,500-plus price range and the price goes down with more companies being monitored for each company added.
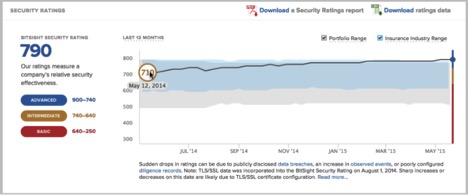
The company shown below (Fortune 500 company name removed) is a great example of how a Bromium End Point Security Solution works for a very large enterprise. The company is three to five years out of date for operating system patching, system hardening, and configuration management, yet the overall company score is considered in the Advanced Stage for cybersecurity. This is proof-point that end point detection technology works and is highly effective at protecting the enterprise. This data is helps chief information security officers benchmark, test, and validate whether company defense mechanisms work against potential cyber threats.
The future of how a company will be measured is to demonstrate a cybersecurity team’s performance. The company ratings chart below has the Fortune 500 company names removed; they are household names that have dismal ratings – and have your sensitive data. When you subscribe to these services, you will have a full picture of what is really happening with your business partners, vendors, and companies that may be under merger and acquisition evaluation.
Competing technology companies have a new sales tool to knock out the competition. From a sales perspective, a competing company with a lower cybersecurity rating can lose a critical business deal because its competitor had a higher cybersecurity rating. Not having the proper risk-rating can be a deal killer. Conversely, cybersecurity can now be a revenue enabler because every small detail does matter in a sales deal and having a better cybersecurity posture will be a deciding factor for future sales deals.
Recently, Mansur Hasib, a long-time CSO and CIO, was interviewed by Mark David, a Canadian journalist for an article in IT Canada Online, and asked about the greatest cybersecurity threat organizations face today. Hasib could think of only one – "the organization chart."
"Cybersecurity failures are a direct result of poor executive strategy in any organization. Executives decide where investments are made and what technology or policies are implemented. I have frequently seen executives wasting funds on completely useless non-strategic projects instead of investing in proper cybersecurity. I think smart investors will do well to pay attention to the organizational structure, CIO empowerment, qualified CIOs and CISOs – even the presence of a CISO," he said. "In any publicly traded organization, if the organization does not even have a CISO, the chances of having a poor cybersecurity posture is very high. If the Chief Financial Officer is in charge of IT and cybersecurity, the organization is likely to be flying blind. These organizations will not be good investments as they are not managing their business risks adequately. Cybersecurity insurance is not enough. In most cases cybersecurity insurance will not pay when there is an absence of due diligence."
Benjamin Franklin's often recited, infrequently adhered to, quote – "an ounce of prevention is worth a pound of cure" – fairly depicts much of the cybersecurity landscape today. An organization's ability to rationalize the overstated weight of an ounce leads to deferring prudent cyber priorities to a later date, ultimately costing it pounds of cost, grief, and reputational damage. Furthermore, spending priorities too often read as a CYA checklist but do not achieve the cyber posture that meaningfully reduces risk and exposure. One immediate consideration organizations should investigate is how to hunt the hunter versus being the prey. Network-hunting solutions – a complement of advanced technology and highly skilled tier-3 cyber analysts (“Network Hunters”) – give organizations an ounce of prevention, dramatically reduce their risk and exposure, and leads to cost reduction (insurance premiums) and avoidance (incident response).
About the Author:
Todd Bell is an international cybersecurity & technology executive that has served as a CISO, CIO, Board of Advisors, and Board of Directors for the Fortune 500 to small companies. He currently serves on the board of Forticode Ltd. See Todd's LinkedIn profile for more details.
Related
Managing editor of Enterprise Technology. I've been covering tech and business for many years, for publications such as InformationWeek, Baseline Magazine, and Florida Today. A native Brit and longtime Yankees fan, I live with my husband, daughter, and two cats on the Space Coast in Florida.