RAND Corp: Manage Security Like a Business

(Source: Duncan Andison)
Organizations must figure out a better way to manage cybersecurity like a business, using metrics to determine the relative return on investment (RROI), and constantly evaluating the lifecycle and effectiveness of their security products and programs in order to protect their reputation and data, a new study by the RAND Corporation found.
In partnership with Juniper Networks, RAND today released "The Defender's Dilemma: Charting a Course Toward Cybersecurity," which discovered cybersecurity experts felt their primary responsibility was to protect their organization's reputation; that an organization's size and software quality play a key role in defenders' strategies, and the Internet of Things (IoT) could dramatically reshape organizations' cybersecurity initiatives and success rates.
"The CISO needs to do a comprehensive risk assessment (comprehensive also means weighing cybersecurity risks against, say, other risks that reduce availability of computing resources)," Martin Libicki, senior management scientist with RAND and an author of the report, told Enterprise Technology. "As for developers and partners, the Target [breach] experience suggests that they assume that partner machines are untrustworthy until proven otherwise."
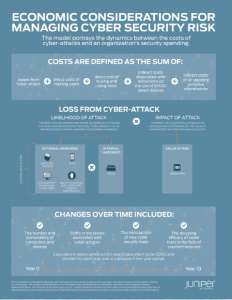
The cost for businesses to manage cybersecurity risk will increase 38 percent over the next decade, RAND estimates, but security executives are uncertain about the protection these investments provide their organizations.
"There is no level playing field between the Black Hats and the defenders," said Rebecca Lawson, senior director of product marketing at Juniper Networks in an interview. "With Black Hats, you have low risk, low cost, and nothing but upside. On the other side, defenders have high risk, high cost, and on a good day you get to keep your job. The inequality is ridiculous."
 The report comes only days after the Office of Personnel Management (OPM) disclosed it was breached, exposing the records of about 4 million current and former employees. Today, the United States Army reportedly took down its website as a preemptive strike against a hacking attempt, and cyberthieves took about $5 million from Irish budget airline Ryanair in April. Hackers used malware to steal millions of dollars from banks, snoop on energy companies, and target Software-as-a-Service providers. With all signs pointing toward increased activity, organization, and sophistication, chief information security officers must take over-arching control over all data and systems and create adaptive policies.
The report comes only days after the Office of Personnel Management (OPM) disclosed it was breached, exposing the records of about 4 million current and former employees. Today, the United States Army reportedly took down its website as a preemptive strike against a hacking attempt, and cyberthieves took about $5 million from Irish budget airline Ryanair in April. Hackers used malware to steal millions of dollars from banks, snoop on energy companies, and target Software-as-a-Service providers. With all signs pointing toward increased activity, organization, and sophistication, chief information security officers must take over-arching control over all data and systems and create adaptive policies.
"CISOs need to find a correct balance between investments in training, tools (particularly those not subject to countermeasures by hackers), device policies, and selective isolation," Libicki said. "As the OPM hack suggests, they also need to institute controls over their databases that can flag unusual activity. Ultimately, they have to find a solution that works for them. In the longer run they may have to look for Internet-facing devices (notably client machines but also web servers) that are more resistant to malware."
Despite the crucial role they play in protecting company data and reputations, many security tools have a half-life and lose value, RAND found, as attackers develop countermeasures to new detection systems. In turn, organizations spend more money to maintain the same level of security; as a result, the effectiveness of these technologies that face countermeasures drops by 65 percent, RAND projects. To combat this, Juniper recommends organizations should invest in technologies and tools not subject to countermeasures and focus on enhanced security management, automation, and policy enforcement.
"Trying to keep pace with the latest cyber threats and worrying about what may happen next keeps many CISOs up at night. However, by taking a small step back and refocusing on managing risks as opposed to attempting to only manage threats helps provide a clearer path forward. Determining a plan isn’t easy. Deciding how to allocate security investments properly and accurately across a business is no small task – believe me, I know. Fortunately, now I can say we have something that can help start such conversations," wrote Sherry Ryan, Juniper Networks' CISO, in a company blog. Juniper Networks developed an interpretation of RAND's heuristic model to create an interactive tool that provides security officers with investment guidance, she added.
Automation, advanced training, and hiring more security staff help organizations protect themselves from attackers – and safety improves over time. Those organizations with "very high levels of security diligence" cut the costs of managing security risk by 19 percent in the first year and 28 percent by year 10, versus those organizations with "very low diligence," RAND found.
" Companies are not taking optimal investment strategies. The report talks about return on managing risk to investment or reduction on risk to investment, but the idea is you have to understand how you invest and where and it differs, depending on your organization's factors. It's not unlike health, in that what I eat influences my mood, and my mood influences whether I exercise," Lawson said.
Hackers continue to use old vulnerabilities. Simply by halving the frequency of software vulnerabilities, organizations would cut the overall cost of cybersecurity by one-fourth, the report found.
" The solution to unpatched systems will have to lie in network management systems that can effectively query devices to understand their patch level," Libicki said. "But another part of the solution is turning off unnecessary applications (e.g., Java) that are particularly vulnerable."
But the new area of IoT could dramatically reshape the security landscape. If organizations properly apply management policies and technologies, then IoT could produce security savings; if companies struggle to apply security controls, IoT could increase the losses due to cyberattacks by 30 percent over a decade, RAND predicted. Organizations also must determine how they construct IoT implementations, said Libicki.
"It is one thing for IoT devices to capture information for internal processing; it is another for them to be given decision-making authority over processes or have access to organizational databases," he said. "If these distinctions are understood IoT deployments can be safer."
Related
Managing editor of Enterprise Technology. I've been covering tech and business for many years, for publications such as InformationWeek, Baseline Magazine, and Florida Today. A native Brit and longtime Yankees fan, I live with my husband, daughter, and two cats on the Space Coast in Florida.










