Cisco Survey Sees Evolving Security Threats
IT infrastructure and the applications they deliver along with emerging open-source web frameworks remain the most attractive targets for hackers and cyber-criminals, according to new web security research data.
Cisco Systems' annual security report released this week also found that security vulnerabilities are beginning to shift away from Java exploits, long the most prevalent and severe, along with server vulnerabilities. Java exploits declined 34 percent in 2014 as a result to improved security, the survey found. That had prompted attackers to look elsewhere for network vulnerabilities to exploit.
Hence, hackers are now focusing on "client-side vulnerabilities" in Adobe Flash Player, the Microsoft Internet Explorer browser and the Apache Struts open-source web framework.
"The growing number of Apache Struts Framework exploits is an example of the trend toward criminals compromising online infrastructure as a way to expand their reach and ability during their attacks," the security survey concluded. Cisco cited the popularity of Apache Struts as "a logical starting point for exploits."
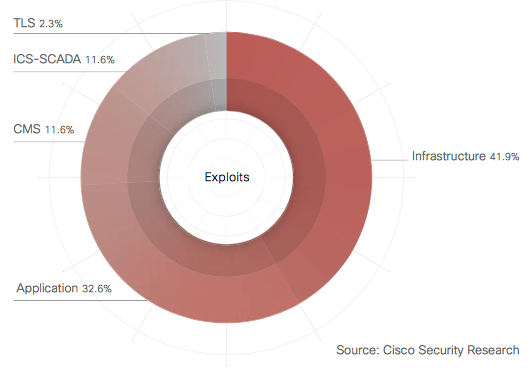
Network infrastructure, applications remain vulnerable to hackers.
Overall, Cisco found that infrastructure attacks accounted for nearly 42 percent of all exploits in 2014 followed by applications at 32.6 percent. Nevertheless, the number of annual threat alerts associated with new and updated product vulnerabilities actually declined in 2014 for the first time in several years.
Despite the growing number of high-profile security breaches last year, Cisco attributed the surprising decline in what it classifies as "cumulative annual alerts" to greater vendor attention to software testing and development. "Improved development lifecycles appear to reduce the number of vulnerabilities that criminal can easily exploit," the survey added.
A security capabilities benchmark study also revealed "disconnects" in how IT administrators view security readiness. Cisco reported that 59 percent of chief information security officers were satisfied with network security defenses while only 46 percent of front-line security operations managers thought they had bullet-proofed their infrastructure and applications.
Along with concerns about infrastructure and application security is the growing use of new exploits such as phony digital security certificates known as secure sockets layer, or SSL, certificates. Cisco found that many systems remain vulnerable to SSL attacks, especially as outdated versions of software are exploited. An examination of Internet-connected devices using OpenSSL certificates revealed that 56 percent used versions of the security certificates that were more than 50 months old.
That means recent Transport Layer Security flaws discovered last year likely remain because many enterprises are failing to keep up with the latest versions of OpenSSL, the security survey warned.
Still, the desire for greater privacy protections has prompted individuals and companies to adopt SSL encryption and "always on HTTPS". But some worry that the growing use of "transport encryption" can ultimately help hackers conceal malware or allow some network operators to issue fake security certificates.
Such was the case earlier this year when the inflight wireless provider Gogo was caught issuing phony SSL certificates, a practice that highlighted the unintended consequences that can include using the technology to conceal malware.
Malware attacks remain one of the biggest threats to enterprise infrastructure, many emanating from Eastern Europe. The Cisco survey warned that network security for multinational companies would continue to be threatened as long as international data governance policies remain uneven.
Related
George Leopold has written about science and technology for more than 30 years, focusing on electronics and aerospace technology. He previously served as executive editor of Electronic Engineering Times. Leopold is the author of "Calculated Risk: The Supersonic Life and Times of Gus Grissom" (Purdue University Press, 2016).










